Most often, computer hackers leave a trail of destruction in their wake: defaced websites, stolen credit card numbers, crippled infrastructure. But in recent years, a band of software devotees who call themselves ethical hackers have made valuable behind-the-scenes contributions to keep social media safe for billions of internet users. They have made it their mission to test the security systems of websites and report flaws to the administrators.
These hackers do it for the appreciation and the money that comes with it. As part of its bounty programmes, Facebook doled out an average of $1,343 for 196 bugs exposed by Indian hackers – the most by any country. One such hacker is Anand Prakash, a security engineer, who hacked popular restaurant discovery and search startup Zomato last week and gained access to 62 million accounts on the site.
Prakash, who works as a security engineer with Flipkart, found that there was a leak in Zomato’s database recall system that allowed him to access private information from all the registered accounts by simply replacing his own user id with someone else’s. Explaining the drill, he posted the whole procedure, as well as the vulnerabilities in the site's programming, on his blog and even created a video as proof of his access.
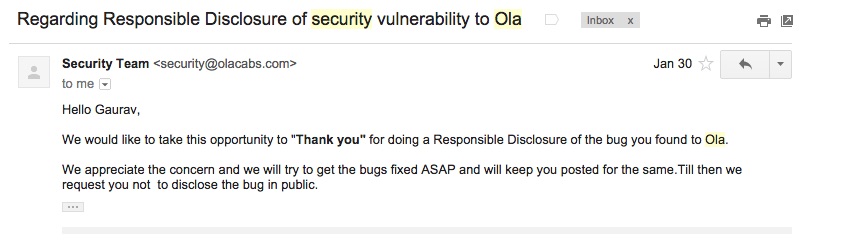
Prakash, who had received $12,000 from Facebook for exposing a major security flaw in the website just a few months ago, did not mean any harm. He reported the bug to Zomato’s engineering team as well as its CEO Deepinder Goyal and the leak was fixed within a few hours.
“Zomato was very responsive to my emails when I told them about the issue,” he told Scroll. “Facebook had even rewarded me, but Zomato thanked me for this and they fixed it pretty soon so that nobody could take advantage of the same.”
Not so receptive
However, all companies aren't so responsive, nor are all hackers so selfless.
Last week, a hacker from Pakistan who goes by the name Mak Man managed to gain access to the huge database of user credentials on the popular music streaming site Gaana.com. Soon enough, the website was down "for maintenance" as he took to the social media to inform people about his act and how he gained access to the database.
Following this, Satyan Gajwani, CEO of Times Internet, the company which runs Gaana.com, commented on this Facebook post and assured Mak Man that the issues flagged by him had been noted and the company would work on fixing it. According to the hacker, he didn’t use the user database or keep a copy of it with himself after the fix was applied.
This, however, didn’t stop him from complaining about the company’s tardy response the last time he had exposed the same flaws. Gajwani had to apologise for this and said, "We've asked Makman if he'd be willing to work with us and help us find any other issues as well."
“I don’t think your intention is to expose personal information about Gaana users, but to highlight a vulnerability," he commented on the post. "Consider it highlighted, and we’re 100% on it. Can I request that you take down access to the data, and delete it completely?”
Three-minute job?
On the weekend, another hacker claimed that he had gained access to the database of Olacabs, a taxi aggregation platform like Uber. According to a reddit post made by TeamUnknown which claimed responsibility for the act, the hack was tricky but it gave them access to user accounts and unused voucher codes.
“Once we got to the database it was like winning a lottery," the post stated. "It had all the user details along with credit card transaction history and unused vouchers. The voucher codes are not even out yet. It's obvious that we wont be using credit card details and voucher codes.”
However, TeamUnknown added that they did not plan to use any of the information. “It’s obvious that we won’t be using credit card details and voucher codes,” the post said, and claimed that they had sent an email to the company on this but received no response.
However, Ola claimed that there was “no security lapse whatsoever” and that the hackers had only gained access to one of the model developing platforms which had dummy data used for internal testing. “We confirm that there has been no attempt by the hackers to reach out to us in this regard.”
This is not the first time that people have pointed out Ola’s vulnerabilities. In March, two hackers claimed to have gained access to the transaction system on the app that allowed them to recharge their Ola Wallet accounts by any amounts without paying anything. "All this takes less than three minutes to perform,” one of the hackers told Business Standard. The company duly noted the bug this time and fixed it.
Tight purse strings
Stories abound about such hackers who managed to get hired by the likes of Facebook or Google after they were able to access internal database of information after breaching corporate security walls. Prodigies who publicise their work often go on to earn a name for themselves, including job offers and huge bounties from multinationals.
He further claimed that the company didn’t respond, despite repeated attempts to reach out. According to the post, contacting the CEO didn’t help either as they received nothing but a thanks. “Almost a month-and-a-half month later, I’m still waiting for a reply or an acknowledgement (and I naively thought it was just customer support that sucks at Ola),” he wrote.
Prakash feels that many more people would be inclined to find bugs on Indian startups instead of running to Facebook or Google if they could expect to be appreciated or rewarded. “The rewards motivate people to find bugs, I do this all the time on Facebook because they take quick action and also provide rewards,” he said. “Indian startups are very thankless when it comes to acknowledging someone’s work on their problems.”
These hackers do it for the appreciation and the money that comes with it. As part of its bounty programmes, Facebook doled out an average of $1,343 for 196 bugs exposed by Indian hackers – the most by any country. One such hacker is Anand Prakash, a security engineer, who hacked popular restaurant discovery and search startup Zomato last week and gained access to 62 million accounts on the site.
Prakash, who works as a security engineer with Flipkart, found that there was a leak in Zomato’s database recall system that allowed him to access private information from all the registered accounts by simply replacing his own user id with someone else’s. Explaining the drill, he posted the whole procedure, as well as the vulnerabilities in the site's programming, on his blog and even created a video as proof of his access.
Prakash, who had received $12,000 from Facebook for exposing a major security flaw in the website just a few months ago, did not mean any harm. He reported the bug to Zomato’s engineering team as well as its CEO Deepinder Goyal and the leak was fixed within a few hours.
“Zomato was very responsive to my emails when I told them about the issue,” he told Scroll. “Facebook had even rewarded me, but Zomato thanked me for this and they fixed it pretty soon so that nobody could take advantage of the same.”
Not so receptive
However, all companies aren't so responsive, nor are all hackers so selfless.
Last week, a hacker from Pakistan who goes by the name Mak Man managed to gain access to the huge database of user credentials on the popular music streaming site Gaana.com. Soon enough, the website was down "for maintenance" as he took to the social media to inform people about his act and how he gained access to the database.
Following this, Satyan Gajwani, CEO of Times Internet, the company which runs Gaana.com, commented on this Facebook post and assured Mak Man that the issues flagged by him had been noted and the company would work on fixing it. According to the hacker, he didn’t use the user database or keep a copy of it with himself after the fix was applied.
This, however, didn’t stop him from complaining about the company’s tardy response the last time he had exposed the same flaws. Gajwani had to apologise for this and said, "We've asked Makman if he'd be willing to work with us and help us find any other issues as well."
@satyangajwani #makman #gaana #Indiatimes pic.twitter.com/N4DvnQt1Rq
— Mak Man (@themakmaniac) May 28, 2015“I don’t think your intention is to expose personal information about Gaana users, but to highlight a vulnerability," he commented on the post. "Consider it highlighted, and we’re 100% on it. Can I request that you take down access to the data, and delete it completely?”
Three-minute job?
On the weekend, another hacker claimed that he had gained access to the database of Olacabs, a taxi aggregation platform like Uber. According to a reddit post made by TeamUnknown which claimed responsibility for the act, the hack was tricky but it gave them access to user accounts and unused voucher codes.
“Once we got to the database it was like winning a lottery," the post stated. "It had all the user details along with credit card transaction history and unused vouchers. The voucher codes are not even out yet. It's obvious that we wont be using credit card details and voucher codes.”
However, TeamUnknown added that they did not plan to use any of the information. “It’s obvious that we won’t be using credit card details and voucher codes,” the post said, and claimed that they had sent an email to the company on this but received no response.
However, Ola claimed that there was “no security lapse whatsoever” and that the hackers had only gained access to one of the model developing platforms which had dummy data used for internal testing. “We confirm that there has been no attempt by the hackers to reach out to us in this regard.”
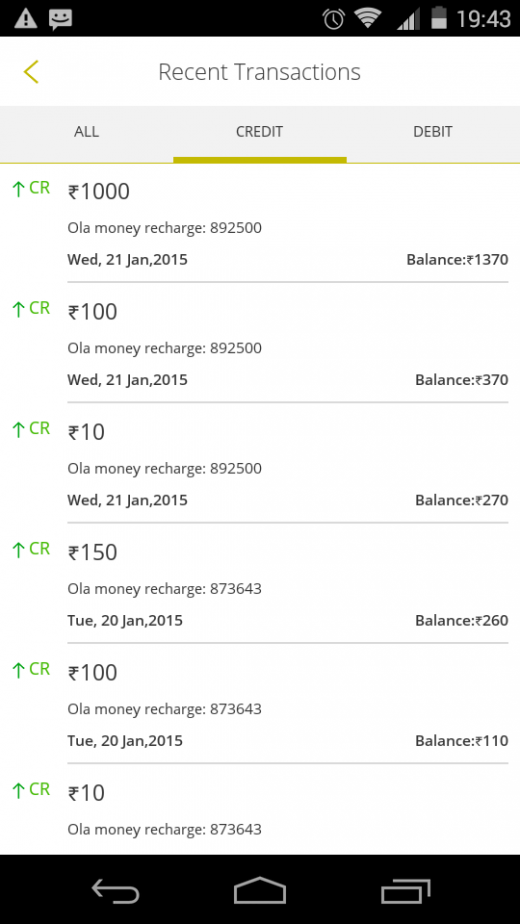
This is not the first time that people have pointed out Ola’s vulnerabilities. In March, two hackers claimed to have gained access to the transaction system on the app that allowed them to recharge their Ola Wallet accounts by any amounts without paying anything. "All this takes less than three minutes to perform,” one of the hackers told Business Standard. The company duly noted the bug this time and fixed it.
Tight purse strings
Stories abound about such hackers who managed to get hired by the likes of Facebook or Google after they were able to access internal database of information after breaching corporate security walls. Prodigies who publicise their work often go on to earn a name for themselves, including job offers and huge bounties from multinationals.
In the past, many such cases have come up where hackers have claimed to breach security of some of the popular Indian tech-startups and posted their modus operandi online, resulting in company taking notice faster than it would through an email.
“It’s easier to grab attention when it’s on a blog or the social media,” said Prakash. “Most companies don’t even respond to hackers when they point out bugs and only some go as far as thanking them for saving them crores of rupees in losses and PR disasters.”
Prakash is not alone. Many hackers have felt that Indian companies are not the best when it comes to acknowledging their security flaws or rewarding those who manage to reveal them. Shubham Paramhans, one of the two people who claimed to have hacked into Ola Wallet, wrote in this blogpost how Ola gave a “very ugly and rude response” when they asked about bug bounty programs.
via thenextweb
He further claimed that the company didn’t respond, despite repeated attempts to reach out. According to the post, contacting the CEO didn’t help either as they received nothing but a thanks. “Almost a month-and-a-half month later, I’m still waiting for a reply or an acknowledgement (and I naively thought it was just customer support that sucks at Ola),” he wrote.
Prakash feels that many more people would be inclined to find bugs on Indian startups instead of running to Facebook or Google if they could expect to be appreciated or rewarded. “The rewards motivate people to find bugs, I do this all the time on Facebook because they take quick action and also provide rewards,” he said. “Indian startups are very thankless when it comes to acknowledging someone’s work on their problems.”
Limited-time offer: Big stories, small price. Keep independent media alive. Become a Scroll member today!
Our journalism is for everyone. But you can get special privileges by buying an annual Scroll Membership. Sign up today!